Datasets
In this paper, we used a DJI Mini 3 drone to capture images across various campus environments. A total of three scenes with distinct geometric characteristics were recorded. In addition, we incorporated two public datasets from the OMMO…
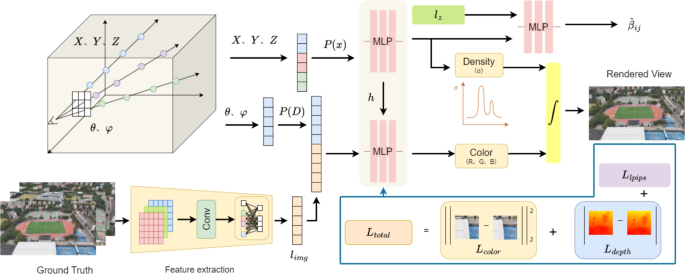
In this paper, we used a DJI Mini 3 drone to capture images across various campus environments. A total of three scenes with distinct geometric characteristics were recorded. In addition, we incorporated two public datasets from the OMMO…
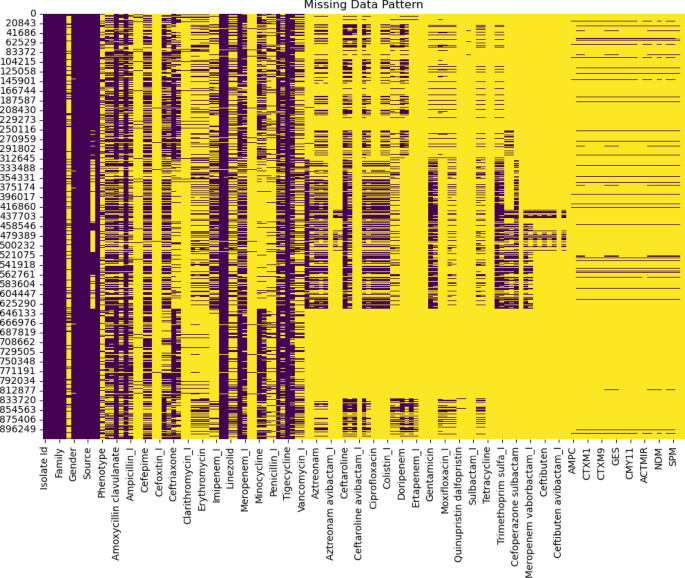
EDA was performed using matplotlib, pandas, and seaborn libraries to understand the underlying distributions and correlations in the dataset. The dataset has 917,049 rows with information on resistance interpretations of…
Time fractional derive (AB) with fractional order \(\kappa\) is defined as follows42:
$$^{AB}{_i} \wp_{b}^{i} f(t) = \frac{h(k)}{{(1 – k)}}\smallint_{i}^{b} P_{q} \frac{{ – k(b – t)^{k} }}{1 -…
The three experts pairwise compared and rated all the indexes in order to objectively evaluate the weight of each index. Combined with the triangular fuzzy preference scale shown in Table 1, the…
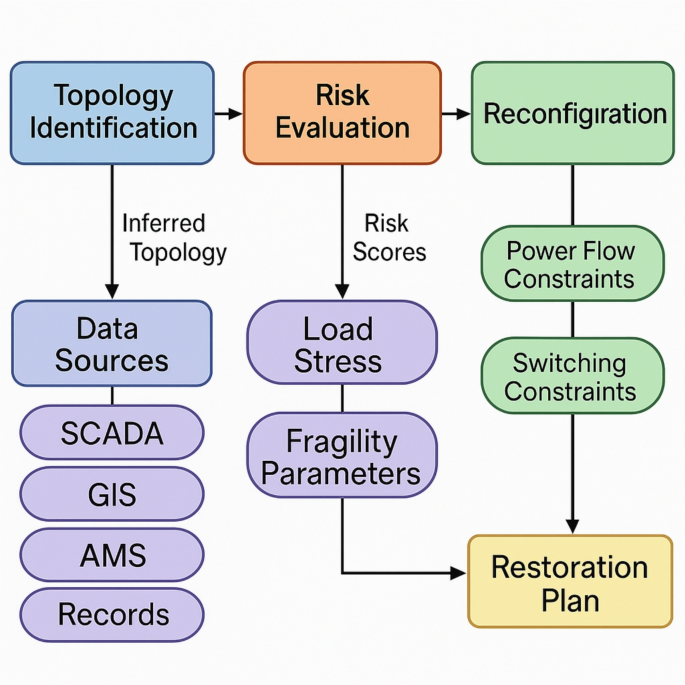
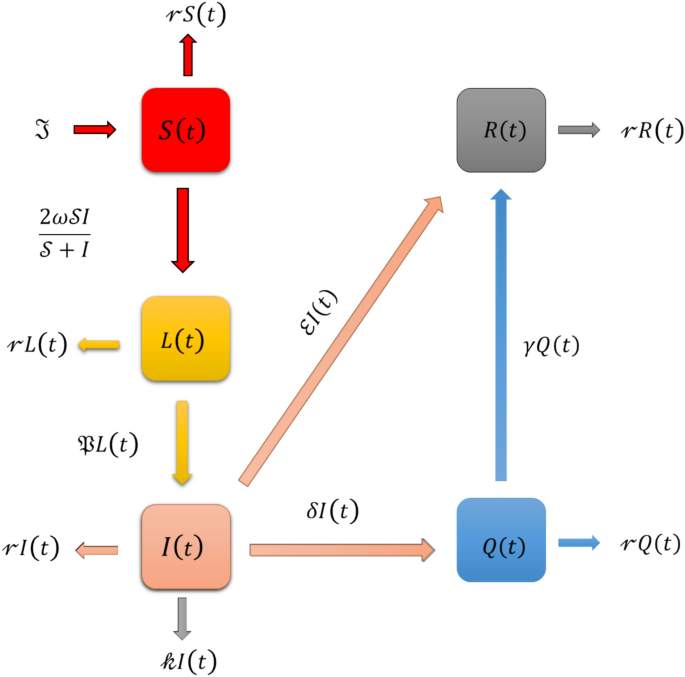
Integrated Framework for Data-Driven Topology Identification, Risk Evaluation, and Reconfiguration in Distribution Networks.
Figure 1 presents a structured schematic of the proposed data-driven framework for resilient distribution system…
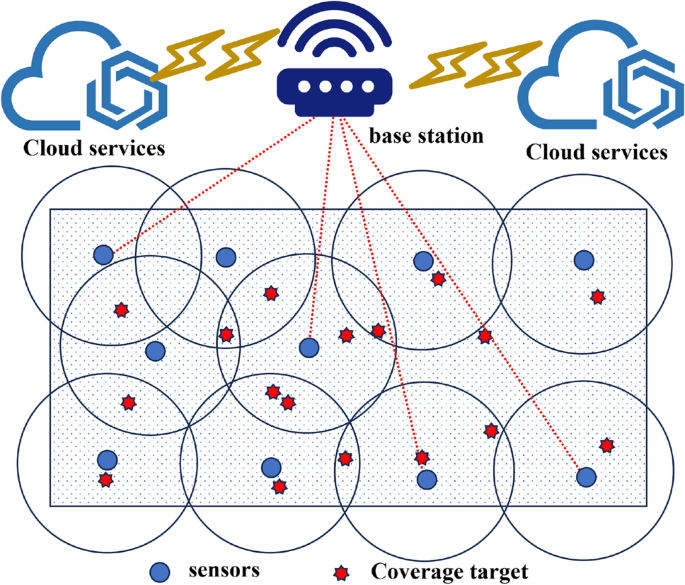
To address the challenge of high-dimensional state spaces in wireless sensor network (WSN) coverage and sensing deployment, a novel hierarchical state representation method is proposed. This approach not only…
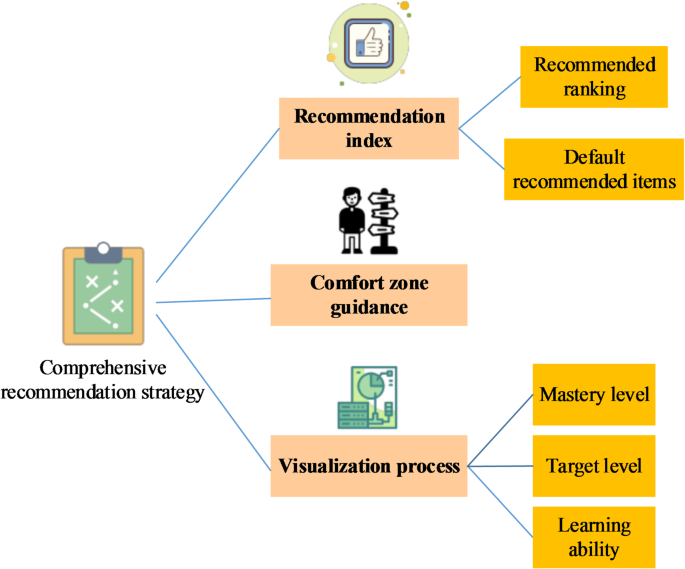
In higher education, English teaching is considered a crucial subject, and its teaching quality and assessment effectiveness have always been a focus of attention1,2,3. Traditional methods for evaluating English…
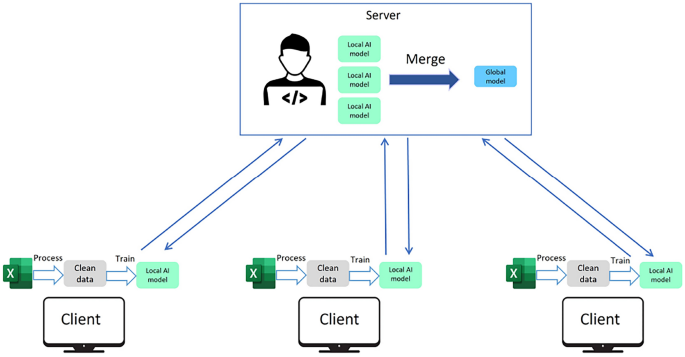
The related work is divided on two sections. First we provide, the backgroung on Federated Learning, Split Learning, and SplitFed Learning. Subsequently, we will discuss the security aspects of these methods.
The basic…
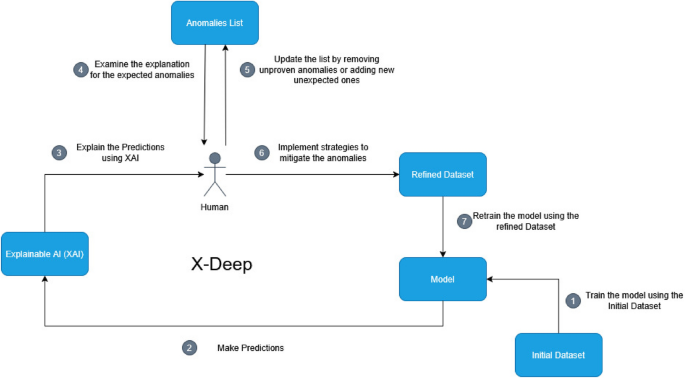
This section presents the results of the four sets of experiments described in Section “Approach”.
An exploratory data analysis phase was conducted to characterize the corpus and help decide on an appropriate…
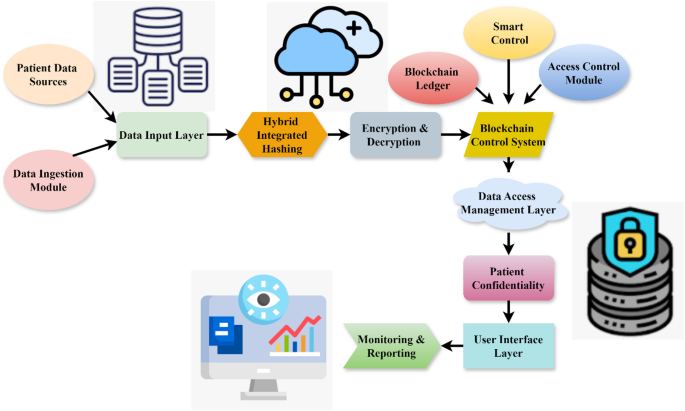
The proposed PDA-HIHM system has three key characteristics that improve the security of healthcare data access First, it presents a hybrid hashing technique that combines traditional SHA-256 with entropy-based dynamic chaining, improving…