Let \(Y_{ij}\) denote the observed biomarker measurement for the i-th individual at time \(t_{ij}\), where \(i = 1, \dots , n\) represents the individuals in the dataset, and \(j = 1, \dots , n_i\) represents the time points for repeated…
Category: 7. Maths
-
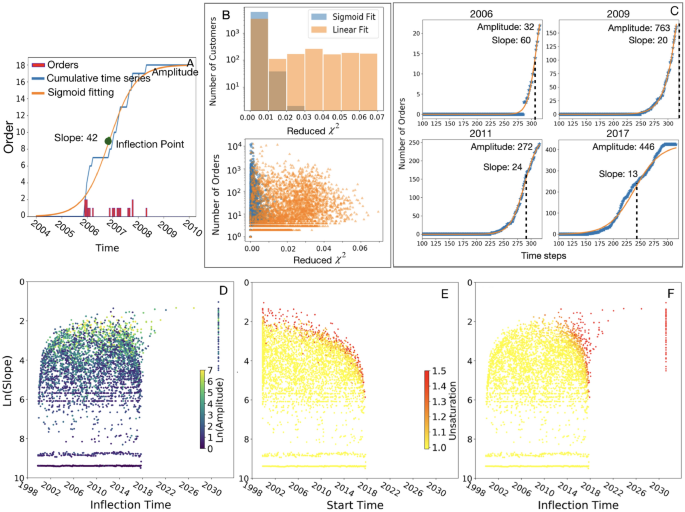
Predicting system dynamics of pervasive growth patterns in complex systems
A sigmoidal curve is defined by three key parameters: inflection point, slope, and amplitude. Here, we show that the evolution of the fitted parameters provides a clear understanding of the current state of activity and can make reliable…
Continue Reading
-
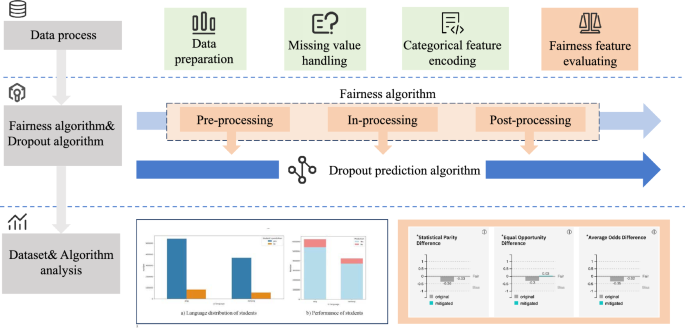
FairEduNet: a novel adversarial network for fairer educational dropout prediction
Our experimental evaluation was designed to be comprehensive, assessing fairness from both a data and an algorithmic perspective. First, we conducted a preliminary analysis on three educational datasets to identify any inherent biases in the…
Continue Reading
-
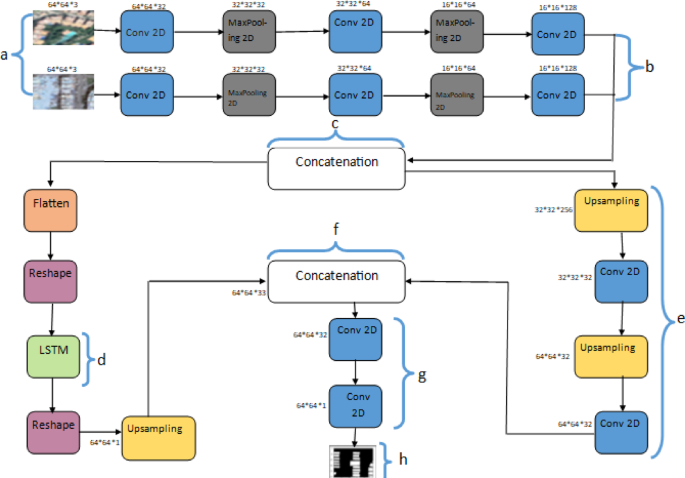
Spatial temporal fusion based features for enhanced remote sensing change detection
Bachmann-Gigl, U. & Dabiri, Z. Cultural heritage in times of crisis: Damage assessment in urban areas of ukraine using Sentinel-1 SAR data. ISPRS Int. J. Geo-Inf. 13(9), 319. https://doi.org/10.3390/IJGI13090319 (2024).
…
Continue Reading
-
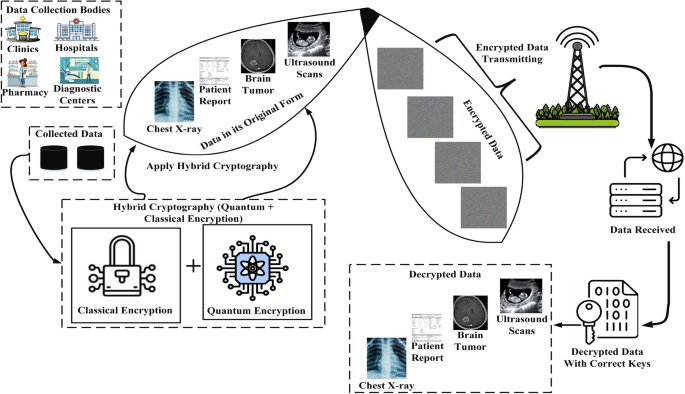
Fusion cryptography for secure medical data transmission using mathematical quantum computing operations
The proposed cryptosystem is evaluated through several analyses, including lossless analysis, computational complexity analysis, and correlation analysis. Furthermore, the encryption’s robustness is evaluated against attacks, including noise,…
Continue Reading
-
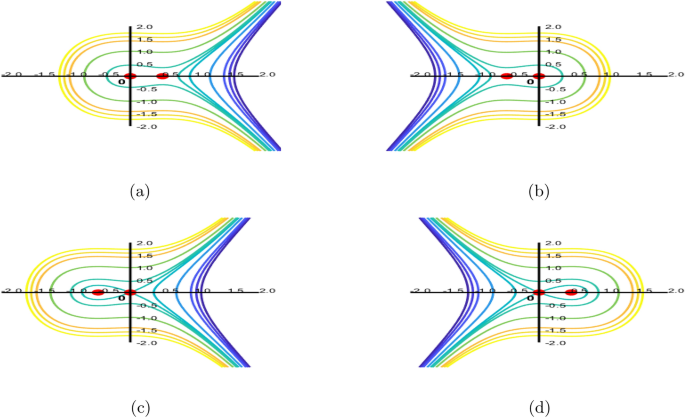
Dynamical description and analytical study of traveling wave solutions for generalized Benjamin-Ono equation
Considered the wave transformation as
\(u(x,y,t)=\phi (\eta )\), where \(\eta =ax+by-\gamma t\).
Taking the derivatives and submit into the \(eq.(1)\) and get the ODE as
$$\begin{aligned} a^{4}\phi ^{(4)}+\phi ”\left( \gamma ^{2}c_{1}-c_{2}\gamma…
Continue Reading
-
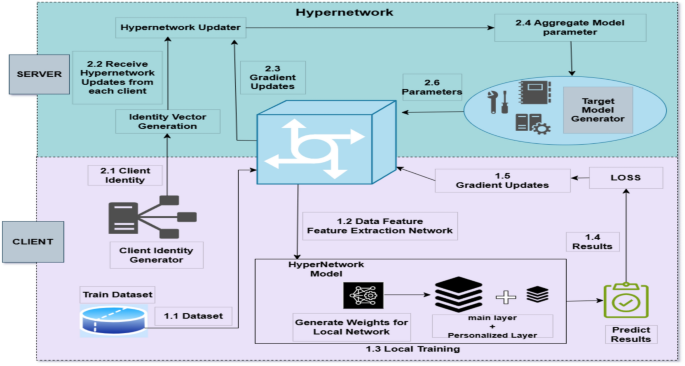
A personalized federated hypernetworks based aggregation approach for intrusion detection systems
The ResNet family33 is a prominent design for Convolutional Neural Networks (CNN). The network consists of several convolutional layers, resulting in a substantial quantity of convolutional filters. The hyper-network served as the primary…
Continue Reading
-
A predictive approach to enhance time-series forecasting
Traditional KD involves transferring probabilistic class information between two models that share the same representation space. In our approach, we reformulate this student-teacher dynamic by placing the teacher model in the relative future of…
Continue Reading
-
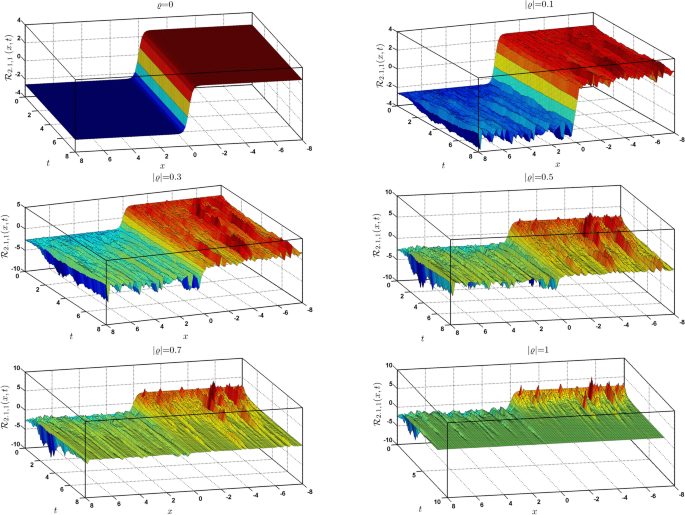
Identification of stochastic optical solitons in a generalized NLSE characterized by fourth order dispersion and weak nonlocality
This section makes use of the IME tanh function approach to build every potential solution for Eq. (3). For this aim, we suppose the following wave transformation:
$$\begin{aligned} \mathcal {R}=\mathcal {H}(\zeta )\ e^{i \left( \beta x-\omega t…
Continue Reading
-
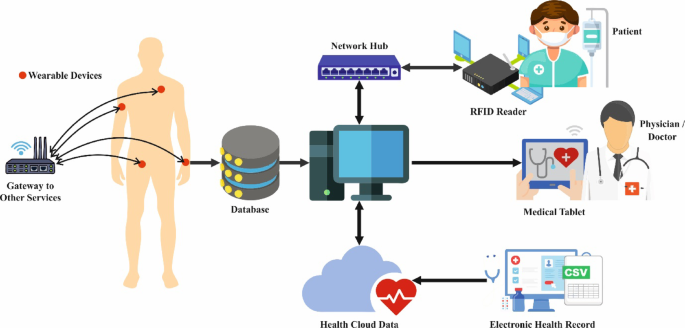
Improving internet of health things security through anomaly detection framework using artificial intelligence driven ensemble approaches
This paper presents a new EIoHTSCD-SEGO method. The method’s key intention is automatically classifying anomaly detection using AI-based data science approaches. It encompasses three processes: data pre-processing involving feature vector and…
Continue Reading
