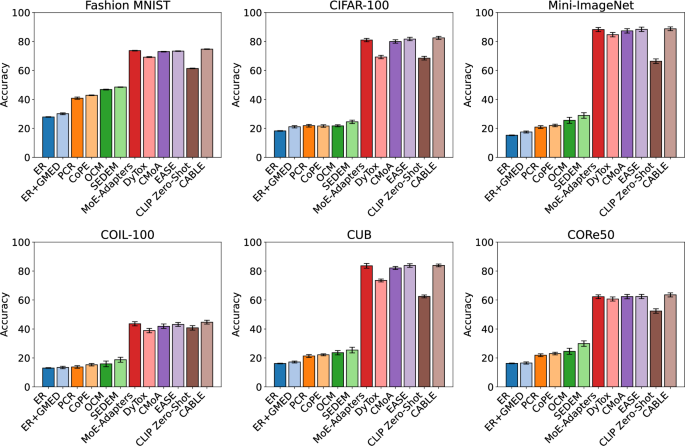
This section details a new method for adapter-based, task-free continual learning utilizing a policy optimization approach to decide tasks. First, we provide preliminaries for the method. After, we describe detecting negative inputs by…
Category: 7. Maths
-
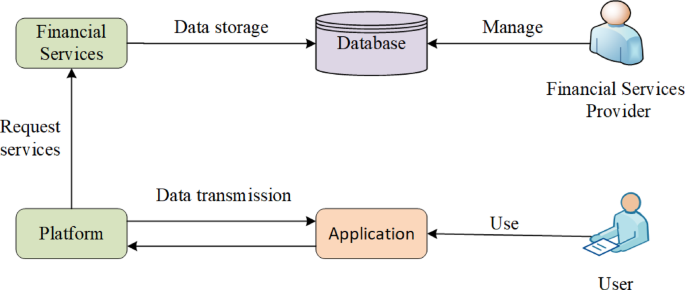
Comprehensive assessment of privacy security of financial services in cloud environment
To validate the effectiveness of the above assessment method, two financial services providers are evaluated in this paper. The first is a financial services provider specializing in financial investment and securities trading, whose services…
Continue Reading
-
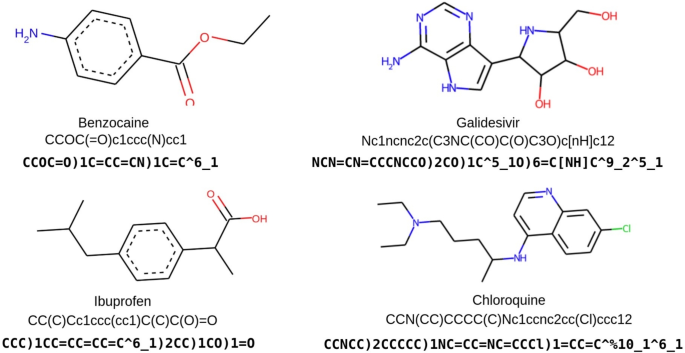
PCF-VAE: posterior collapse free variational autoencoder for de novo drug design
Molecule representation
The significance of data representation becomes critical in the domain of data-assisted methodologies, such as DL. A variety of representations, such as SMILES, graphs, fingerprints, and three-dimensional models, provide…
Continue Reading
-
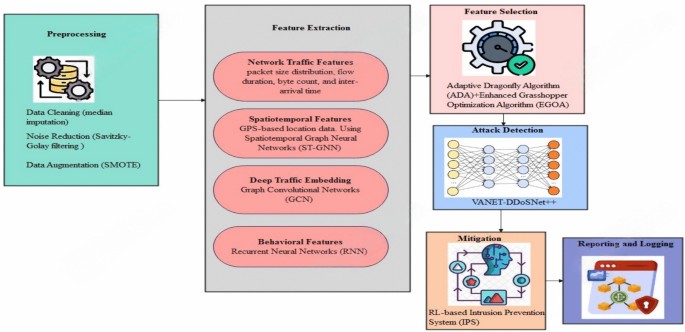
A hybrid deep learning model for detection and mitigation of DDoS attacks in VANETs
The proposed approach as illustrated in Fig. 1 seeks to improve the detection and mitigation of DDoS attacks in VANET by deploying different strategies at different levels. The End-to-end model is manifested in Fig. 2 and the Pseudocode for the…
Continue Reading
-
Estimating the peak age of chess players through statistical and machine learning techniques
According to the January 2024 ELO list published by FIDE, there are 1,814 players worldwide holding the GM title. Of these, 38 players fall within the super GM category, although historically, 131 players have surpassed the 2,700 ELO threshold….
Continue Reading
-
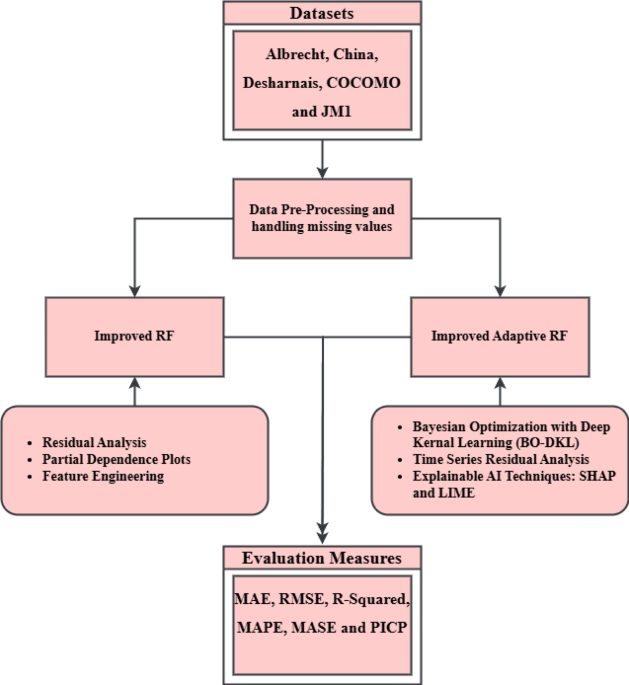
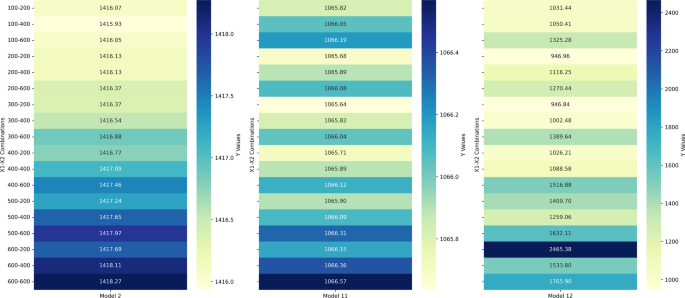
Enhancing software effort estimation with random forest tuning and adaptive decision strategies
During training, random forests (RF) generate a large number of individual decision trees. In order to arrive at the final prediction, the mean prediction for regression or the mode of the classes for classification is computed by aggregating the…
Continue Reading
-
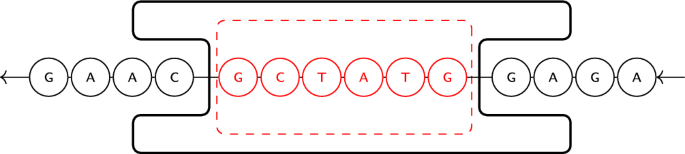
Constrained coding for error mitigation in nanopore-based DNA data storage
In this section, we will discuss the construction of the proposed constrained codes, as well as the encoding and decoding processes. An overview of the data storage system is shown in Fig 3. The figure shows both a Core Pipeline focused on the…
Continue Reading
-

A two-stage joint model approach to handle incomplete time dependent markers in survival data through inverse probability weight and multiple imputation
Let \(Y_{ij}\) denote the observed biomarker measurement for the i-th individual at time \(t_{ij}\), where \(i = 1, \dots , n\) represents the individuals in the dataset, and \(j = 1, \dots , n_i\) represents the time points for repeated…
Continue Reading
-
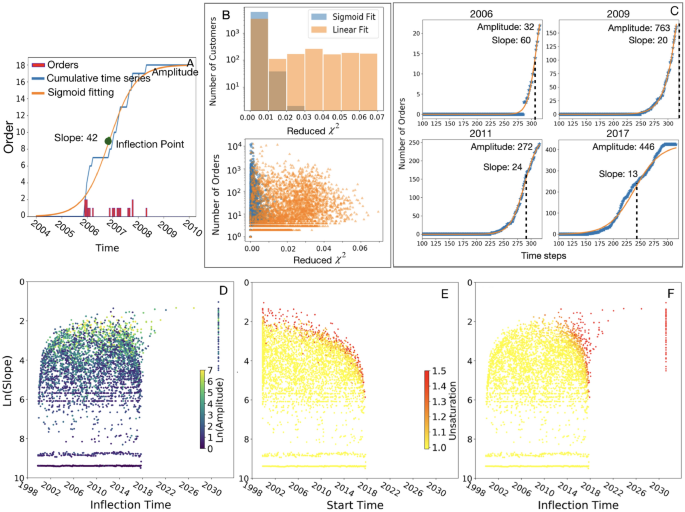
Predicting system dynamics of pervasive growth patterns in complex systems
A sigmoidal curve is defined by three key parameters: inflection point, slope, and amplitude. Here, we show that the evolution of the fitted parameters provides a clear understanding of the current state of activity and can make reliable…
Continue Reading
-
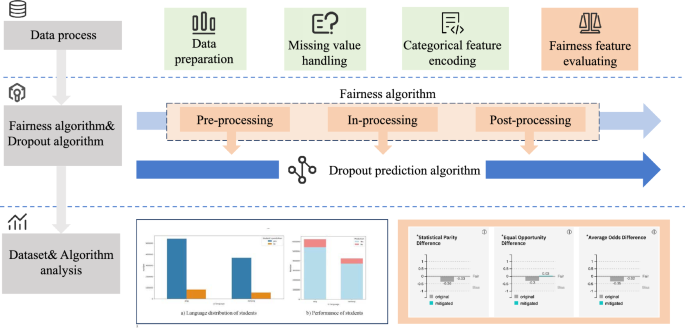
FairEduNet: a novel adversarial network for fairer educational dropout prediction
Our experimental evaluation was designed to be comprehensive, assessing fairness from both a data and an algorithmic perspective. First, we conducted a preliminary analysis on three educational datasets to identify any inherent biases in the…
Continue Reading