In Eq. 3, \(\:{C}_{\text{i}\text{n}\text{f}}\) indicates the ability of CTLs to infiltrate the TME. Under control conditions without treatment, \(\:{C}_{\text{i}\text{n}\text{f}}=1.0\). In irradiated targets, \(\:{C}_{\text{i}\text{n}\text{f}}\)…
Category: 7. Maths
-

Leveraging large language models for pandemic preparedness
Leveraging large language models for pandemic preparedness
Continue Reading
-

Modeling eye gaze velocity trajectories using GANs with spectral loss for enhanced fidelity
Generative adversarial networks
A variety of probabilistic models describe animal movement by considering the position as an output of a deterministic function \(G\) applied to a sampler of random latent variables. For example, in correlated…
Continue Reading
-

The outcome prediction method of football matches by the quantum neural network based on deep learning
Application concept of QNN technology in football prediction
In today’s highly digital and data-driven era, accurate predictions of football match outcomes have been a prominent research area. The emergence of QNN technology presents a new…
Continue Reading
-

A lightweight scalable hybrid authentication framework for Internet of Medical Things (IoMT) using blockchain hyperledger consortium network with edge computing
Although managing resources at the edge, particularly in the context of highly dynamic IoMT environments, remains a significant limitation, such as scalability and optimization, edge computing can reduce the computational burden on centralized…
Continue Reading
-
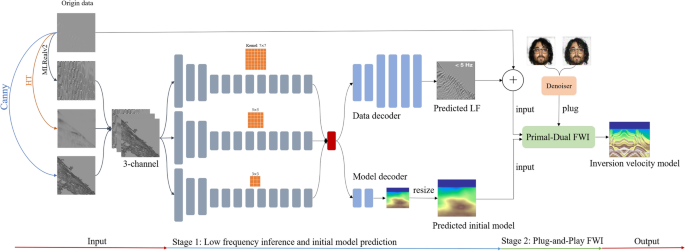
Progressive plug and play full waveform inversion with multitask learning
This section describes the network architecture, loss function, training data construction, and implementation details of MCNN in turn.
Network architecture
Figure 1 shows the overall framework of the proposed algorithm. The first stage is the…
Continue Reading
-
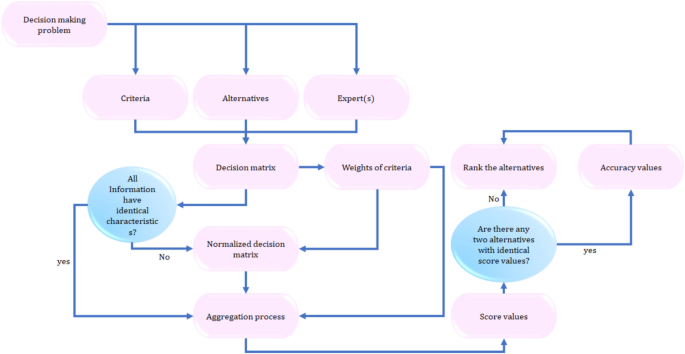
Decision-making using quasirung orthopair fuzzy exponential aggregation operators for carbon capture technology selection
In this section, we will apply the proposed aggregation operators to address MCDM problems in the \(p,q\)-QOF framework. To facilitate this, we introduce the following assumptions and notations:
-
\(\Lambda…
Continue Reading
-
-
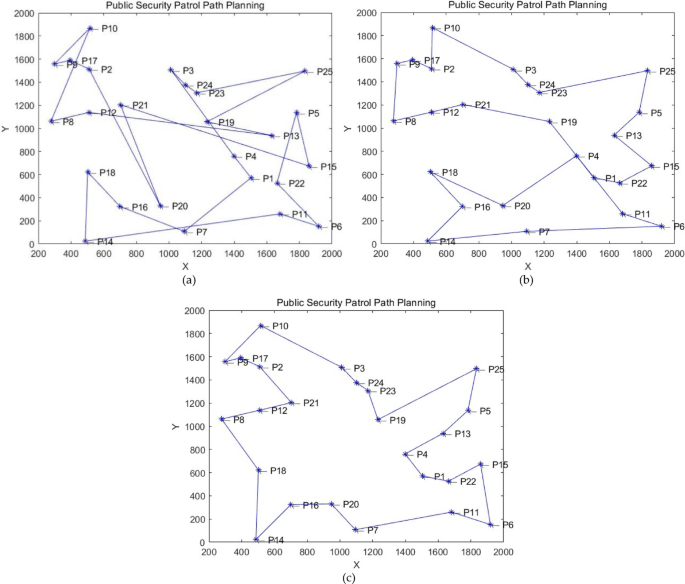
Public security patrol path planning recommendation method based on wolf-pack optimization algorithm using DAF and BRS
Swarm intelligence optimization
In nature, a variety of creatures with limited individual abilities demonstrate remarkable capabilities through group formations and inter-individual information exchange, such as ant colonies, bee colonies, and…
Continue Reading
-
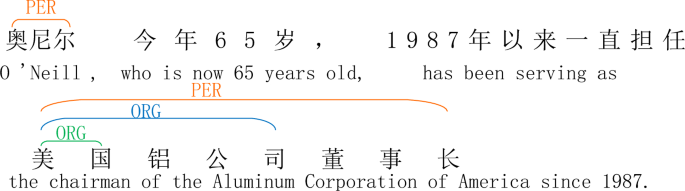
Transformer-based prototype network for Chinese nested named entity recognition
In this study, we propose a transformer-based prototype network (MSTPN) for the CNNER method that utilizes entity bounding boxes to identify nested named entities, where each entity bounding box consists of an entity category label and length….
Continue Reading
-
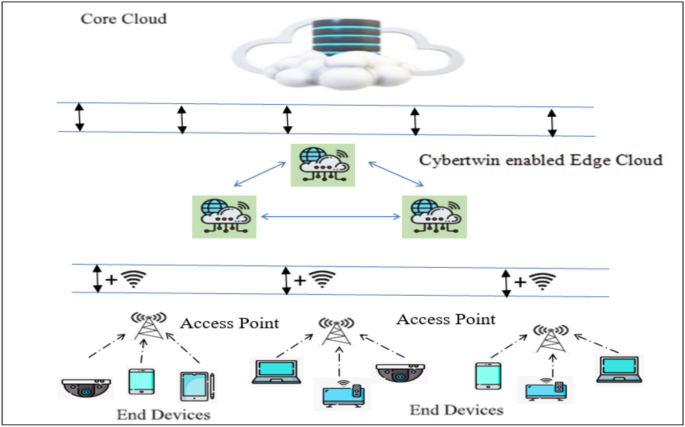
Efficient joint resource allocation using self organized map based Deep Reinforcement Learning for cybertwin enabled 6G networks
A cybertwin-enabled edge-end cloud network is analyzed, as depicted in Fig. 1, structured into three level hierarchies23. The lower layer has various end devices like smartphones, smart sensors, and smart vehicles, all supporting diverse…
Continue Reading
