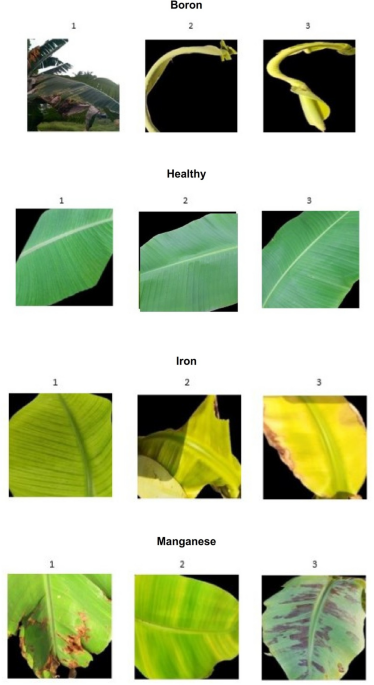
This paper proposes an ensemble model using NAS optimization for diagnosing the major micro nutrient deficiencies, such as boron, iron and manganese, in banana crops. The Data were collected from the publicly available fully labelled Mendeley…
Category: 7. Maths
-
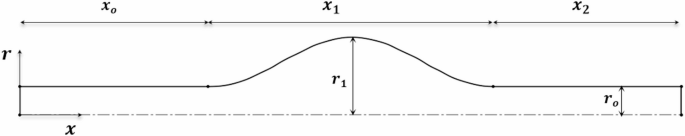
Numerical simulation of red blood cells migration and platelets margination for blood flow in micro-vessels with fusiform aneurysms
The cellular blood flow in micro-vessels with a fusiform is examined under different values of hematocrit. The migration of the RBCs and the platelet margination process are considered, especially in the aneurysm region. Other hemodynamics…
Continue Reading
-
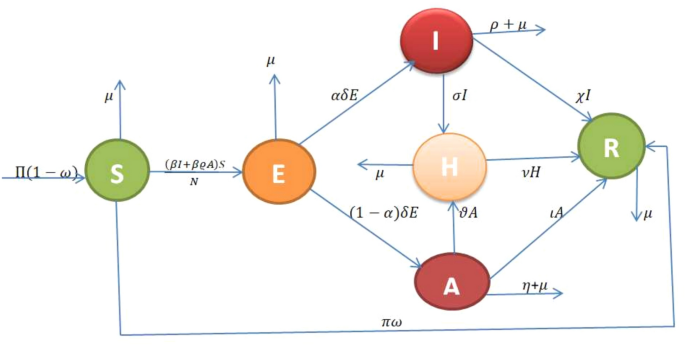
Optimal control and economic evaluation of diphtheria disease model with booster immunization and hospitalization
Positivity and boundedness of solutions
The non-negativity of the parameters and variables in the model (1) is biologically significant since the model represents the dynamics of a human disease. Therefore, it is essential to demonstrate the…
Continue Reading
-
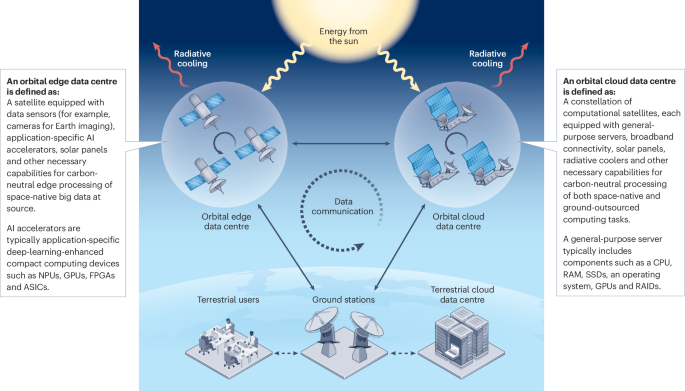
The development of carbon-neutral data centres in space
Masanet, E., Shehabi, A., Lei, N., Smith, S. & Koomey, J. Recalibrating global data center energy-use estimates. Science 367, 984–986 (2020).
Google Scholar
Zhai, Y., Ong, Y.-S. & Tsang, I. W….
Continue Reading
-
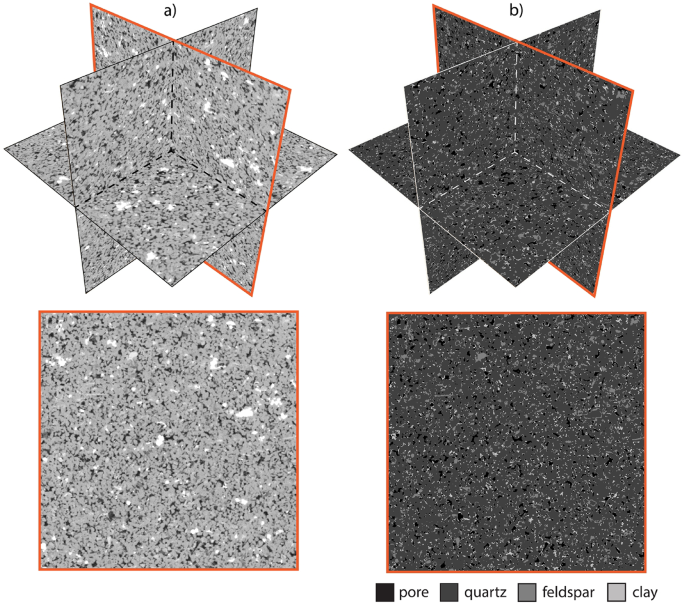
Optimized generative adversarial network for efficient resolution enhancement of 3D segmented rock tomography
Segmented 3D low-resolution training dataset
A Berea sandstone plug with a diameter of 12 mm was prepared to obtain high-quality imaging using a Tescan CoreTOM X-ray micro-CT scanner. The raw 3D micro-CT image acquisition and reconstruction were…
Continue Reading
-

Enhancing the precision of male fertility diagnostics through bio inspired optimization techniques
The proposed methodology outlines a novel, ML based framework for early prediction of male infertility. It integrates clinical, lifestyle, and environmental factors with advanced computational techniques to enable accurate, interpretable, and…
Continue Reading
-
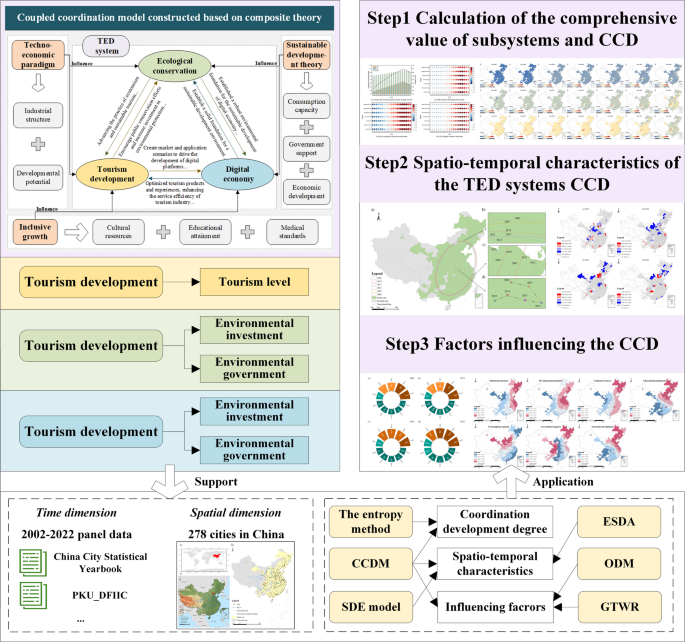
Coupling coordination and driving mechanism between tourism development, ecological conservation and digital economy: insights from Chinese 278 cities
TED subsystem comprehensive development indices calculation and analysis
Based on Eq. 1 to 3 and Table 1, this paper calculates the comprehensive development indices (CDI) and coupling coordination degree (CCD) for the TED subsystems. As shown…
Continue Reading
-
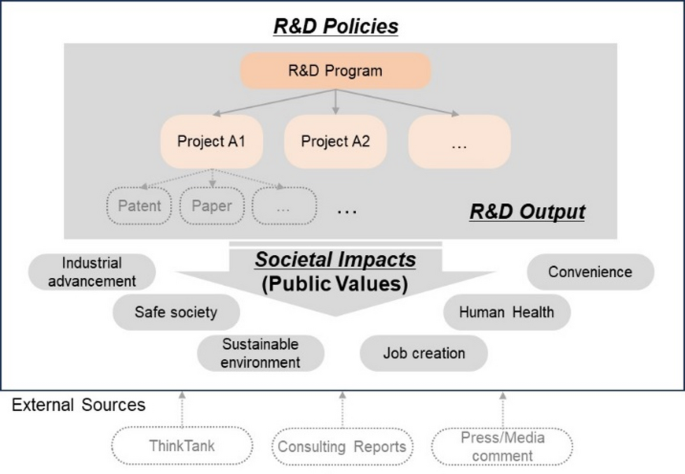
Public values in public R&D through natural language processing
Public values on AI
This study has chosen “Artificial Intelligence (AI)” as the target technology field for analysis. AI is a promising technology area associated with the Fourth Industrial Revolution, with significant links to public value…
Continue Reading
-
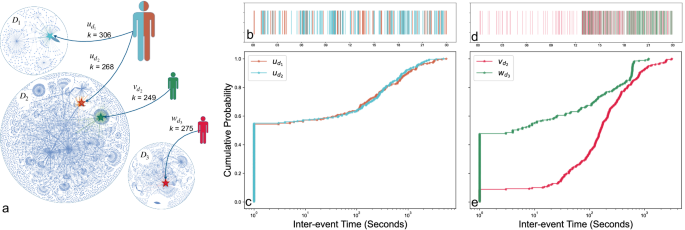
Temporal fingerprints for identity matching across fully encrypted domains
Preliminaries
In this study, we aim at identifying individuals across different encrypted domains. Specifically, we aim at learning an identity matching function:
Definition 1
Given D1, …, Dn different…
Continue Reading
-
Phishing detection on webpages in European non-English languages based on machine learning
This section introduces and evaluates a novel approach to phishing detection tailored for non-English webpages, particularly those in European countries where minor languages are spoken. The first subsection introduces the challenges of phishing…
Continue Reading