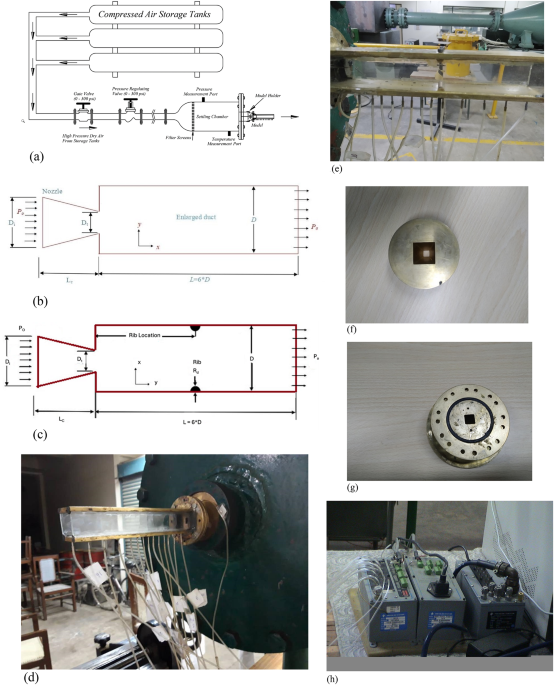
The last few decades have seen the emergence of the exciting field of study known as turbulent base flows. The projectile’s blunt base, the fuselage of an airplane, the blunt base of a shell, etc., are common locations for low and…
Category: 7. Maths
-
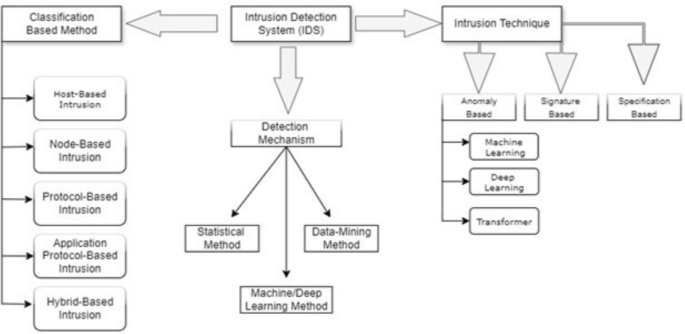
Network intrusion detection model using wrapper based feature selection and multi head attention transformers
Guezzaz, A., Benkirane, S., Azrour, M. & Khurram, S. A reliable network intrusion detection approach using decision tree with enhanced data quality. Security and Communication Networks 2021, 1230593 (2021).
Continue Reading
-
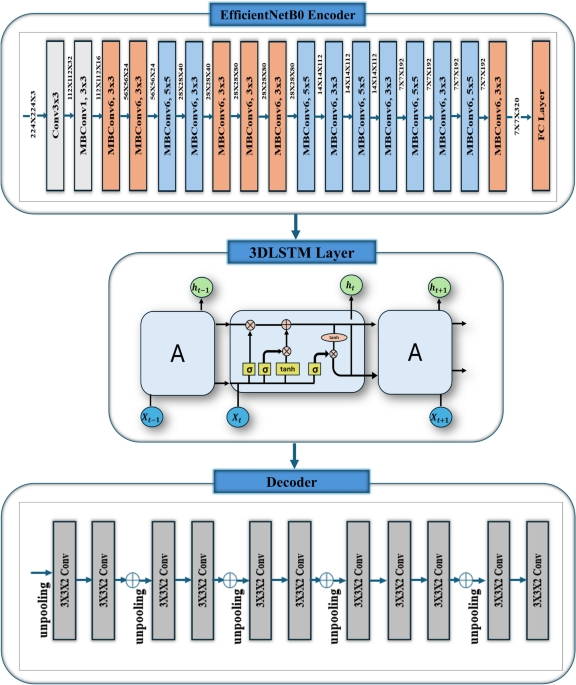
3D reconstruction from 2D multi-view dental 2D images based on EfficientNetB0 model
Erdelyi, R.-A. et al. Dental diagnosis and treatment assessments: Between x-rays radiography and optical coherence tomography. Materials 13(21), 4825 (2020).
Google…
Continue Reading
-
Pyramidal attention-based T network for brain tumor classification: a comprehensive analysis of transfer learning approaches for clinically reliable and reliable AI hybrid approaches
Our proposed pyramidal, convoluted, and attention-driven computer-aided diagnosis system received training through a high-performance GPU setup, which optimized computation and ensured real-time diagnostic capabilities in clinical environments….
Continue Reading
-
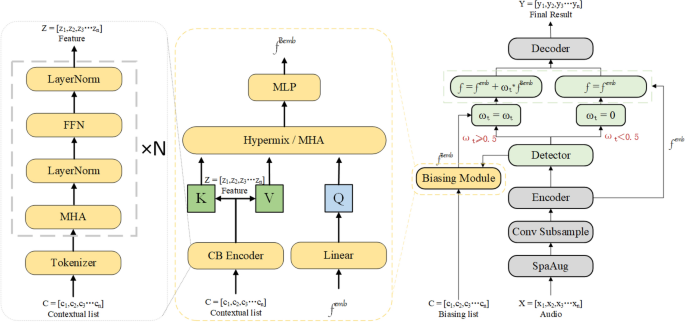
Adaptive context biasing in transformer-based ASR systems
Results on AISHELL
Our approach demonstrates superior competitiveness compared to various mainstream models, as shown in the Table 2. On the AISHELL dataset, the proposed method achieves 5.56 character error rate (CER) on the validation set (Dev)…
Continue Reading
-
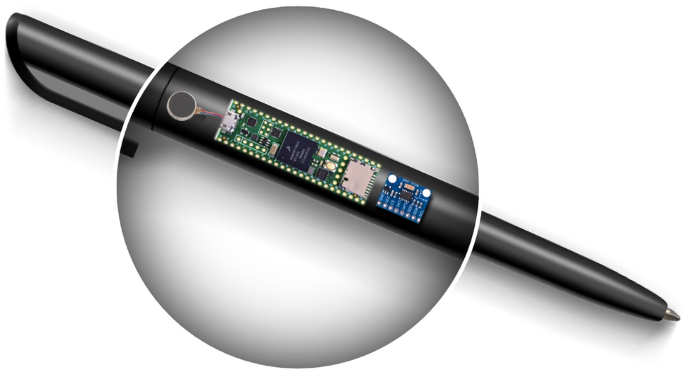
A smart pen prototype with adaptive algorithms for stabilizing handwriting tremor signals in Parkinson’s disease
According to18, adaptive algorithms are widely employed in applications involving signals with unknown or time-varying statistical properties, unlike fixed coefficient algorithms, which have predefined internal parameters and do not adapt to…
Continue Reading
-
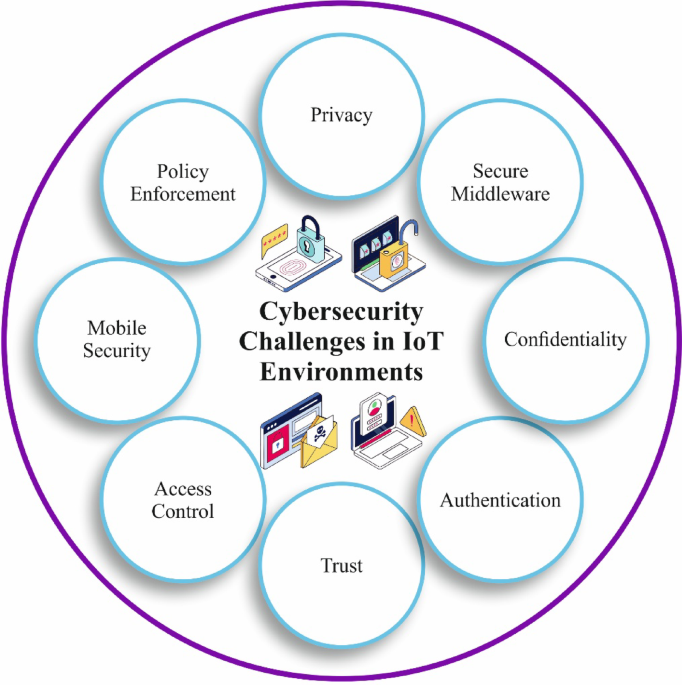
An effectiveness of deep learning with fox optimizer-based feature selection model for securing cyberattack detection in IoT environments
This article proposes the FOFSDL-SCD method. This paper analyses cybersecurity-driven techniques for improving IoT networks’ resilience and threat detection abilities utilizing advanced methods. Data pre-processing, dimensionality reduction…
Continue Reading
-
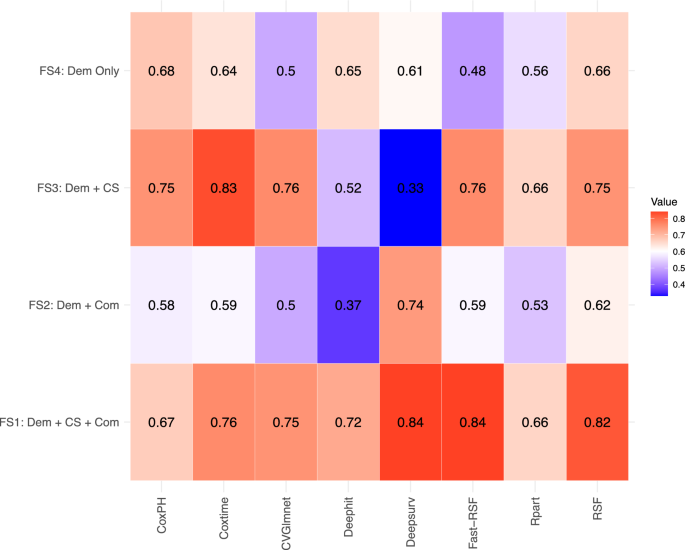
Alzheimer’s disease risk prediction using machine learning for survival analysis with a comorbidity-based approach
Table 1 ADNI and AIBL participants demographic and clinical features summarized in a stratified manner within censored and transitioned groups. Table 2 Performance comparison with previously published studies on the survival Analysis of CN to MCI… Continue Reading
-

Predict the writer’s trait emotional intelligence from reproduced calligraphy
This section explores the construction of a model that combines handcrafted features with deep learning techniques for evaluating calligraphy reproductions. This evaluation requires simultaneous processing of both the reference characters and the…
Continue Reading
-
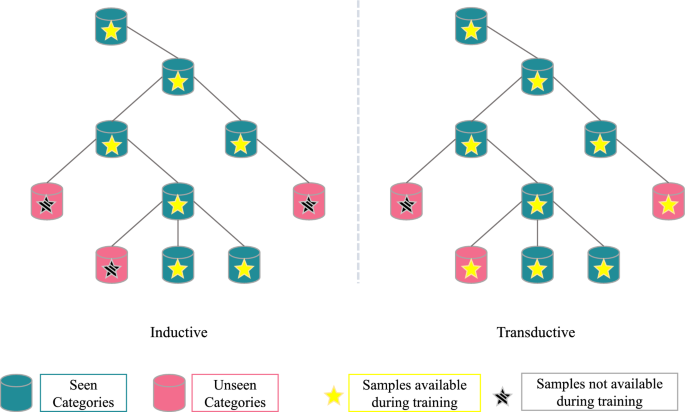
Transductive zero-shot learning via knowledge graph and graph convolutional networks
In this paper, we propose an efficient method for zero-shot learning, based on distilling information of categories from semantic embeddings and knowledge graph representations, enhanced with a transductive strategy based on a Double Filter…
Continue Reading