Imaging and compositional analyses of Onahu
Onahu is in the Otis_Peak formation (fm), recognized by its fluvial deposits of planar laminated and cross-stratified sandstone to granule conglomerates. Large, scattered…
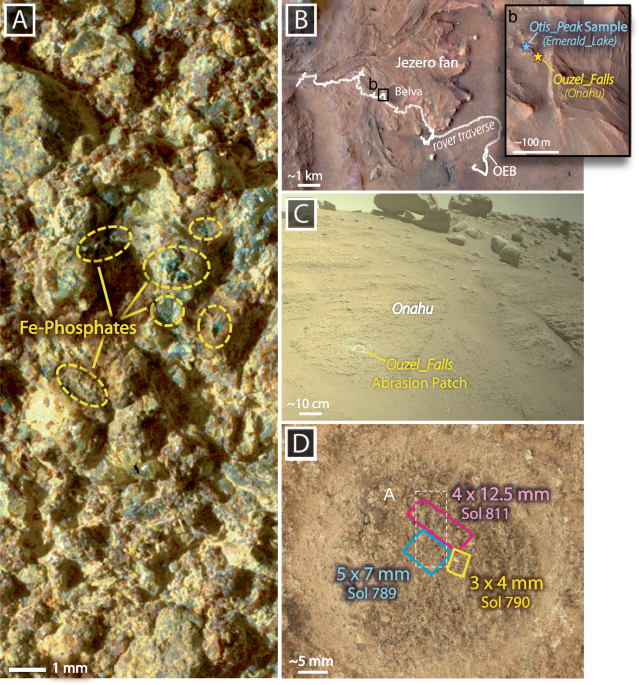
Onahu is in the Otis_Peak formation (fm), recognized by its fluvial deposits of planar laminated and cross-stratified sandstone to granule conglomerates. Large, scattered…

This section proposes an effective method to address the temporal dependency problem and the “many-to-one” problem in sensor fusion semantic segmentation, focusing on reducing the accumulated error and improving the mapping accuracy of depth…
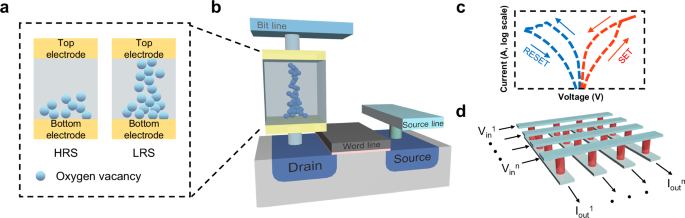
Mii, Y. J. Semiconductor innovations, from device to system. in 2022 IEEE Symposium on VLSI Technology and Circuits (VLSI Technology and Circuits). 276-281.
Horowitz, M. 1.1 Computing’s energy problem (and what we can do about it). in 2014 IEEE…

The proposed methodology combines dual-stream feature extraction with the use of textual representation learning and graph-based social context modeling for enhanced fake news detection. The workflow of proposed study is given in Fig. 1. It…
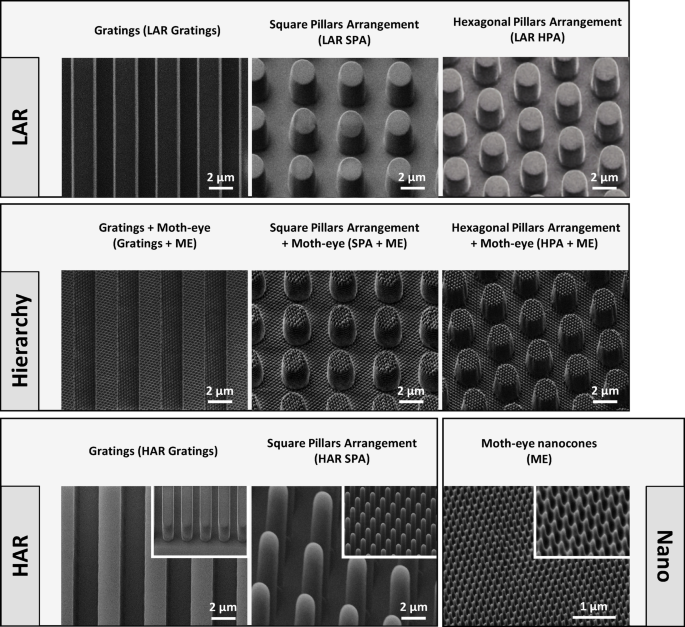
Different nanofabrication processes and techniques have been used to obtain the desired micro- and nanoscale topographies. The nanometric topography involves ME nanocones with approximately 250 nm diameter at the…
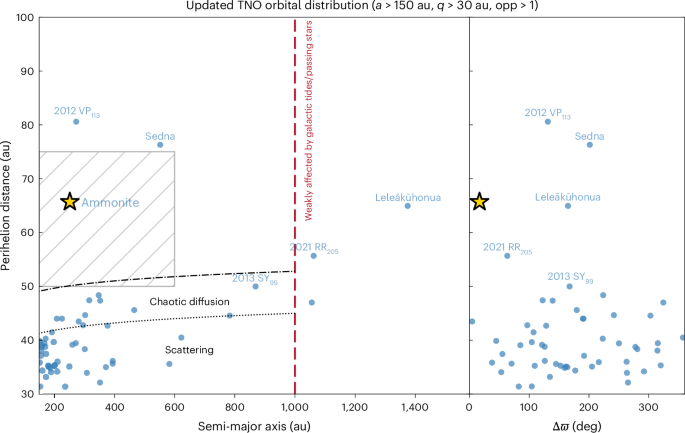
Brown, M. E., Trujillo, C. & Rabinowitz, D. Discovery of a candidate inner Oort cloud planetoid. Astrophys. J. 617, 645–649 (2004).
Google Scholar
Graham, S. & Volk, K. Uranus’s…

This study explores various deep learning models, including AlexNet, MobileNet, ResNet, SqueezeNet, and ConvNeXt, which are tailored for tasks like plant disease detection and classification. These models were chosen for their ability to handle…
Keppler, M. et al. Discovery of a planetary-mass companion within the gap of the transition disk around PDS 70. Astron. Astrophys. 617, A44 (2018).
Google Scholar
Haffert, S. Y. et al. Two…

The proposed medical image encryption algorithm is validated through experimental analysis of a DICOM dataset consisting of 100 Gy-scale DICOM images with a size of 256 × 256 pixels. The simulation analysis is carried out…

A comparative analysis is included in this section to assess the superiority of our proposed method. Tao et al.46 proposed a single-image encryption method that combines optics and chaos, applying the fractional Fourier…